Configuring CheckPoint Identity Awareness
There are five “identity sources” which Identity Awareness can use to acquire identities:-
- AD Query
- Browser-Based Authentication
- Endpoint Identity Agent
- Terminal Servers Identity Agent
- Remote Access
This post describes the basics of how to configure Identity Awareness, integrate with Active Directory (AD Query method) and configure a rule to require authentication for accessing the internet.
Configuring Identity Awareness
Open the properties of the CheckPoint gateway
Tick the “Identity Awareness” software blade
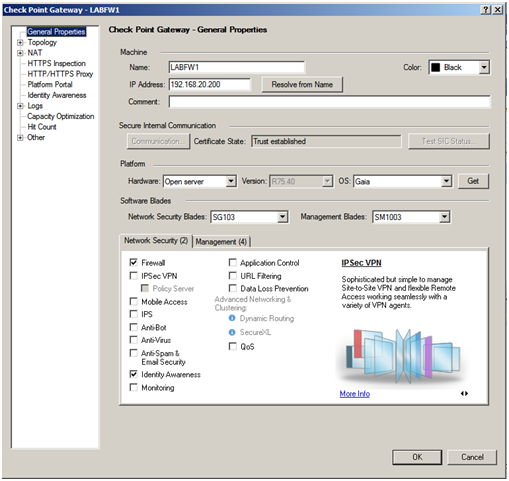
Select the correct gateway that will be used to identify users
Select the “AD Query” method for acquiring identity

Select an Active Directory, entering Domain Administrator credentials when prompted, click Connect to establish a connection
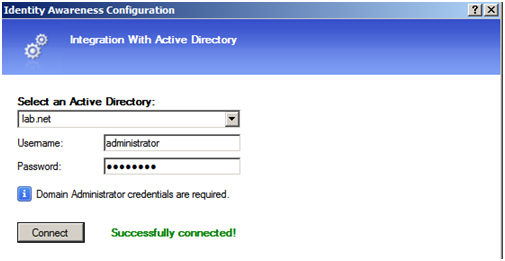
Once the connection between the gateway and Active Directory has been establish go to the “Users and Administrators” tab in SmartDashboard

Right click “Access Roles” and click “New Access Roles”
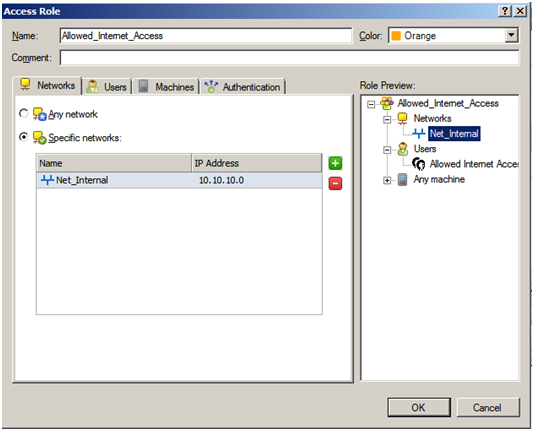
Name the new “Access Role” appropriately eg “Allowed_Internet_Access”

Specify “Networks” if you wish to allow access from
Click the “Users” tab
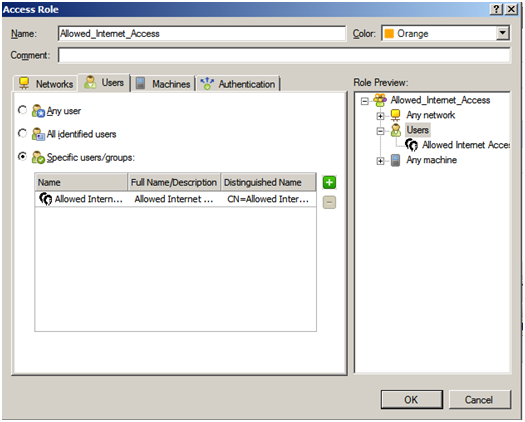
Click “Specific users/groups”, click the green + button and browse to the location of the user or group

Click the “Machines” tab, click the green + button and specify the machines or group of machines you wish to allow access from

Click OK to finish configuration of the new “Access Role”
Either create a new firewall rule or modify an existing rule to specify the source of the new “Access Role”
Before…
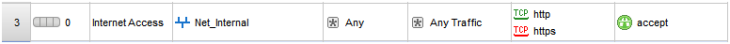
After…

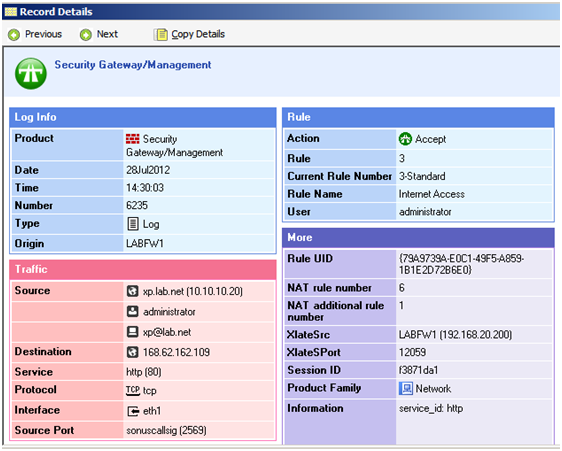
When a user who is a member of the AD group “Allowed Internet Access” is logged on to the computer “XP” from the internal subnet defined as “Net_Internal” they will be allowed access
However the same user accessing the internet from a machine not specified in the access rule will be dropped.
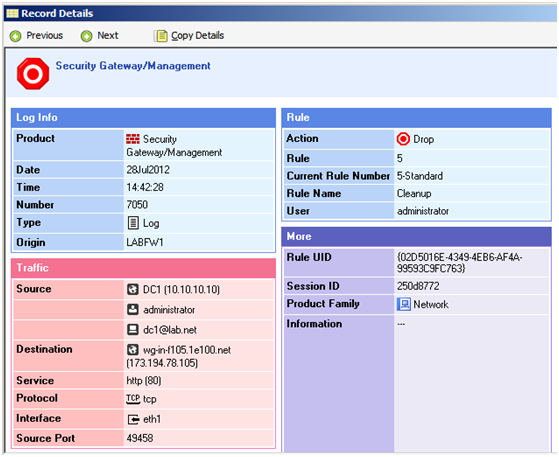
When the user attempts to make the connection and not all conditions are met, the connection will be dropped and NO warning or error message will be displayed. The captive portal webpage could be enabled to prompt the users for a username and password or even explain why they are not allowed access.
In testing in my lab I have found out that a connection which meets network, user and computer conditions will be allowed access, but when the user is logged off and another user logs on who is NOT a member of the correct group allowing internet access they are allowed access. I believe this is because the gateway still assumes the connection is still from the same user/computer source so is therefore access is allowed. In most scenarios this would not matter if the same user used the same computer, I can imagine in schools where users share computers this would be an issue. Further investigation required…..