1. Check Point Firewall: How To Add A Static Route In CLI In Gaia
You don't do this in expert mode. Here is how you add a static route in Gaia in CLI below. It works well if you prefer CLI to the GUI.
CP> set static-route 0.0.0.0/1 nexthop gateway address 5.5.5.5 on
2. CPVIEW
3. Zdebug
5. TCPDump
6. SmartView Tracker
Check Point Firewall: tcpdump In CLI
Do a tcpdump to verify that the packets were actually leaving the firewall. It is. You can see it coming in from the private IP of 10.10.10.10, then being NAT'ed to the public 55.55.55.55 and on to 4.2.2.2.
[Expert@CheckPoint1:0]# tcpdump -i any -vvv dst 4.2.2.2
tcpdump: WARNING: Promiscuous mode not supported on the "any" device
tcpdump: listening on any, link-type LINUX_SLL (Linux cooked), capture size 96 bytes
12:25:20.917906 IP (tos 0x0, ttl 127, id 8280, offset 0, flags [none], proto: ICMP (1), length: 60) 10.10.10.10 > 4.2.2.2: ICMP echo request, id 1, seq 19, length 40
12:25:20.918146 IP (tos 0x0, ttl 126, id 8280, offset 0, flags [none], proto: ICMP (1), length: 60) 55.55.55.55 > 4.2.2.2: ICMP echo request, id 46253, seq 19, length 40
12:25:21.919046 IP (tos 0x0, ttl 127, id 8285, offset 0, flags [none], proto: ICMP (1), length: 60) 10.10.10.10 > 4.2.2.2: ICMP echo request, id 1, seq 20, length 40
12:25:21.919096 IP (tos 0x0, ttl 126, id 8285, offset 0, flags [none], proto: ICMP (1), length: 60) 55.55.55.55 > 4.2.2.2: ICMP echo request, id 46253, seq 20, length 40
12:25:26.863785 IP (tos 0x0, ttl 127, id 8291, offset 0, flags [none], proto: ICMP (1), length: 60) 10.10.10.10 > 4.2.2.2: ICMP echo request, id 1, seq 21, length 40
12:25:26.863884 IP (tos 0x0, ttl 126, id 8291, offset 0, flags [none], proto: ICMP (1), length: 60) 55.55.55.55 > 4.2.2.2: ICMP echo request, id 46253, seq 21, length 40
12:25:27.862351 IP (tos 0x0, ttl 127, id 8293, offset 0, flags [none], proto: ICMP (1), length: 60) 10.10.10.10> 4.2.2.2: ICMP echo request, id 1, seq 22, length 40
Firewalls And NAT'ing And The Traveling Packet
Its an interesting thing to me, that NAT'ing takes place before routing does on most firewalls. So, if your public IP address space was 10.10.10.X/24, and you decided that you wanted to NAT your internal 192.168.1.10 server to the public IP address of 10.4.4.4, you could. Now, you might start to think that "you cant do that" because your 10.4.4.4 is not on your 10.10.10.X/24 address space, right? Well, actually, that is wrong. You actually CAN have a public IP address that is not on your public IP range and have it NAT through to your internal server. Routing at the upstream router certainly poses a problem, but if a packet can make it to your firewall, then you can NAT your traffic to any public IP address you want to, even if its not part of your IP range on your firewall interface.
I actually went through this recently on a certain problem I was having on a Check Point firewall. You see, it was the same thing really. I had a public range of, lets say, 40.40.40.0/25. This gives us 126 usable IP addresses (1-126). However, in the config, they had some NATs that were outside of that range. Now, just so you know, they actually owned the whole /24 of 40.40.40.0. But, on the firewall interface, they had split up this subnet and were not using anything above this range (40.40.40.0/25).
In our example, they had a static NAT translation of 40.40.40.200 pointing to a webserver inside the network at 192.168.1.200. I thought that since it was not on the subnet of the public facing NIC on the firewall, the firewall would try to route it out its default gateway (the upstream router), which would try to send it back and ultimately the TTL would hit 0 and the packet would drop. But, this is NOT what happens. What actually happens is that NAT is checked FIRST.
Below, I have the best explanation (from Cisco) of the process the packet actually takes going through the firewall from the outside to the inside. This process also applies to Check Point as well. Notice that first, the ACL is checked to see if the packet is allowed, then NAT. Notice its not until step 7 and 8 where routing comes into place. Its a very interesting process for sure. Take a walk through the steps below. Its a really good read through.
Steps
1. The packet is reached at the ingress interface. Once the packet reaches the internal buffer of the interface, the input counter of the interface is incremented by one.
2. Cisco ASA first looks at its internal connection table details in order to verify if this is a current connection. If the packet flow matches a current connection, then the Access Control List (ACL) check is bypassed and the packet is moved forward. If packet flow does not match a current connection, then the TCP state is verified. If it is a SYN packet or UDP (User Datagram Protocol) packet, then the connection counter is incremented by one and the packet is sent for an ACL check. If it is not a SYN packet, the packet is dropped and the event is logged.
3. The packet is processed as per the interface ACLs. It is verified in sequential order of the ACL entries and if it matches any of the ACL entries, it moves forward. Otherwise, the packet is dropped and the information is logged. The ACL hit count is incremented by one when the packet matches the ACL entry.
4. The packet is verified for the translation rules. If a packet passes through this check, then a connection entry is created for this flow and the packet moves forward. Otherwise, the packet is dropped and the information is logged.
5. The packet is subjected to an Inspection Check. This inspection verifies whether or not this specific packet flow is in compliance with the protocol. Cisco ASA has a built-in inspection engine that inspects each connection as per its pre-defined set of application-level functionality. If it passed the inspection, it is moved forward. Otherwise, the packet is dropped and the information is logged. Additional security checks will be implemented if a Content Security (CSC) module is involved.
6. The IP header information is translated as per the Network Address Translation/ Port Address Translation (NAT/PAT) rule and checksums are updated accordingly. The packet is forwarded to Advanced Inspection and Prevention Security Services Module (AIP-SSM) for IPS related security checks when the AIP module is involved.
7. The packet is forwarded to the egress interface based on the translation rules. If no egress interface is specified in the translation rule, then the destination interface is decided based on the global route lookup.
8. On the egress interface, the interface route lookup is performed. Remember, the egress interface is determined by the translation rule that takes the priority.
9. Once a Layer 3 route has been found and the next hop identified, Layer 2 resolution is performed. The Layer 2 rewrite of the MAC header happens at this stage.
10. The packet is transmitted on the wire, and interface counters increment on the egress interface.
11. The packet is transmitted on the wire, and interface counters increment on the egress interface.
Below is Check Points explanation in the CP documentation. Very similar.
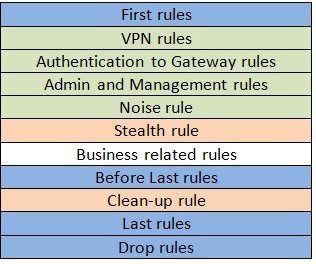
Check Point Firewall: Rulebase Audit
Audit a company's check point firewalls, to see what security items need to be looked at.
Here is a good copy and paste from the best practices sk106597.
The Business related rules section contains the rules that regulate your business traffic.
Business related rules should be grouped together in logical sub-sections to make the format of the rulebase easy to understand.
The sub-sections that are most heavily used should be placed highest in the rulebase (so long as doing this does not compromise SecureXL tuning).
The blue coded rules are the Implied Rules (Policy > Global Properties > Firewall Implied Rules).
The enabled default Implied rules can be selectively turned off if not required or if the administrator has created specific rules to replace them. This is often done to harden or 'nail-down' the rulebase.
The green coded rules are VPN, management and noise rules.
The admin and management rules control access to the firewall e.g. SSH, HTTPS etc. If the implied rules have been disabled then specific rules to permit all required connections to and from the firewalls will be required.
The purpose of the Noise rule is to drop unwanted traffic such as NetBIOS traffic as high up in the rulebase as possible.
The use of a Noise rule helps to make the firewall more efficient by dropping unwanted traffic high up in the rulebase instead of at the bottom of the rulebase (clean-up rule).
If the 'noise' traffic is mixed with 'useful' traffic then additional noise rules can be placed within the Business related rules section to drop the unwanted noise traffic once the useful traffic has been matched.
The Stealth rule should be located as early as possible in the policy, typically placed immediately after the management rules. The purpose of the Stealth rule is to drop unauthorized connections destined to the firewall; protecting the firewall from being scanned and attacked.
The rulebase is likely to be constantly evolving so the effectiveness of the Stealth rule should be periodically tested; it may need to be re-positioned to maintain effectiveness.
The clean-up rule is the last rule in the rulebase and is used to drop and log explicitly unmatched traffic.
To improve the rulebase performance, noise traffic that is logged in the Clean-up rule should be included in the Noise rule so it is matched and dropped higher up in the rulebase.
A "beeping" Check Point management station. running the hardware diagnostics tool off of a USB drive, and it came back clean.
So I ran the command "raidconfig status" and found that I had a hard drive go bad. You will see it says "degraded" and "failed" on drive 2. Time for a replacement.
Smart1> raidconfig status
-- Controller Information --
ID MODEL
C0 MegaRAID SAS 8704EM2
-- Arrays information --
ID Type Size State
C0V0 RAID10 1.816 TB Degraded
-- Disks information --
ID Model Size Status
DISK #1 WD1003FBYX-01Y7B0 931.512GB Online
DISK #2 WD1003FBYX-01Y7B0 931.512GB Failed
DISK #3 WD1003FBYX-01Y7B0 931.512GB Online
DISK #4 WD1003FBYX-01Y7B0 931.512GB Online
Smart1>
2. Check Point Firewall:
How To Push Policy Locally In CLIDid you know that you can "push policy" from CLI? In this case, I have a Check Point 4800 that I want to install the policy on, but not through the GUI. I want to do this in CLI. So, I do the following:
CP>
fw fetch localhostInstalling Security Policy Standard on all.all@CP
Fetching Security Policy from localhost succeeded
CP>